Computing devices and other information systems are capable of leaking data in many peculiar ways.
As malicious entities increasingly target and attack core infrastructures, the IT security methods and policies for protecting highly sensitive and vulnerable locations have been evolving through the years.
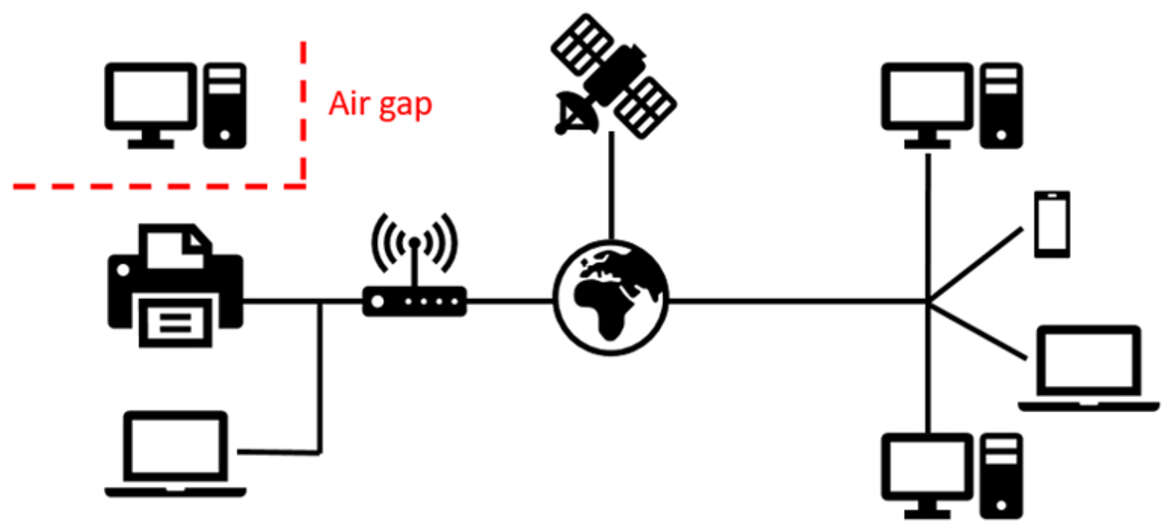
Implementing strong security protocols, such as the “air-gapping” methodology, has the potential to safeguard all vulnerable devices.
Air-gapping is a set of shielding procedures done sequentially in order to ensure the vulnerable computer or any other information system is physically isolated from all unsecured networks, such as the public Internet or an unsecured local area network (LAN).
Air-gapping might include removing all potential data-leaking vectors, such as: Microphones, Speakers, Video cards, Cameras, CD/DVD-ROM drives, Hard disks, Internet cards, USB ports.
Nonetheless, there are also numerous methods to remotely monitor and spy on a computer or information system which require no previous intervention.
It has been demonstrated that it’s possible to monitor the radiation emitted by a cathode ray tube (CRT) monitor or even a modern liquid crystal display (LCD). This form of surveillance is often referred to as Van Eck phreaking or as TEMPEST.
It’s also feasible to listen to a computer’s keyboard with a parabolic microphone and log individual keystrokes without actually requiring logging malware/software.
Even the high-frequency noises emitted by a computer’s CPU can include sensitive information about the programs or instructions being executed.
Due to the broad spectrum and dissimilar nature of all air-gap covert channels, they are frequently placed in categories according to the physical channel in which they operate in, such as:
- Physical Media
- Acoustic
- Light
- Seismic
- Magnetic
- Thermal
- Electromagnetic
Acoustic
Hackers frequently take advantage of acoustic covert channels because they are erroneously regarded as innocuous and inconsequential by the uninitiated. However, all computers and their accompanying paraphernalia, such as printers, keyboards, mice, cooling fans, processors and most other information systems emit ultrasonic sounds. These sounds can be captured by either generic microphones (for short distances) or parabolic microphones (for long distances) and then can be deciphered in order to reconstruct intelligible data.
“Fansmitter” is the quintessential example of a malware that can acoustically exfiltrate sensitive information from vulnerable air-gapped computers, even when no speakers or audio hardware audio are present, because it utilizes the noise emitted from the CPU and chassis fans.
“DiskFiltration” is another complex data processing software which is able to exfiltrate data using acoustic signals emitted from the hard drive by manipulating the movements of the hard drive actuator and using seek operations, thus making the hard drive “move” in specific ways which generate sound.
Physical Media
Even though spreading malware through physical media is nowadays mostly obsolete, in the past, this was the main way computers got infected with malicious software. Approximately 2-3 decades ago, tangible information vectors such as floppy disks and CD-ROMs were the malignant medium of choice for all hackers, but currently, viruses like “Stuxnet” are primarily transmitted through USB drives. The Stuxnet computer worm bridges the air-gap with the help of a USB drive so it can then send/receive requests to and from the operator via a hidden storage area created in raw FAT (File Allocation Table) structure.
Light
Apart from the self-evident and prime source of light emissions for any computer system, i.e. the monitor (either a CRT or LCD), sensitive light emanations can be leaked through other vectors, such as the keyboards LEDs, printers or modems.
It’s possible to reconstruct a CRT screen’s contents by analyzing the light intensity of the display’s diffuse reflection off a nearby wall. Whereas, the contents of an LCD screen could be reconstructed by analyzing diffuse reflections off objects within relatively close proximity of the display, such as eyeglasses, bottles and even cutlery up to 30 meters away, if strong enough telescopic lenses are employed.
In more nuanced cases, certain type of software can transmit ASCII data by modulating the Caps Lock LED with serial data at 50 bits/s. Similar to Morse code signaling, the irregular blinking of the LED will not raise suspicion in the average computer user.
Other malware can infect a computer on an air-gapped network and make it receive and send attack commands through a multi-function printer/scanner that the computer is connected to.
Thermal
All electronic devices generate excess heat and require thermal management to improve reliability and prevent premature failure. Computers are no exception. This is usually done with fans and we’ve already seen how they can be abused to provide an exfiltration channel. Changes in temperature are shown to be an effective, albeit painfully slow, data channel.
Malware can be used to remotely control and internet-connected air-conditioning system using a one-way thermal covert channel. Certain programs are able to bridge the air-gap between adjacent compromised computers (up to 40cm) by using their heat emissions and built-in thermal sensors to create a covert bidirectional communication channel (up to 8 bits per hour).
Seismic
Seismic or vibrational communication is a process where the exchange of data and information is happening through mechanical oscillations or vibrations. Under certain conditions, it’s entirely possible to induce legible vibrations through a computer’s speaker. Moreover, almost all phones and smartphones have the ability to produce seismic waves using their vibration generator.
It has been publically demonstrated that a certain type of malware can be successful in reconstructing the keystrokes typed on a keyboard located in close proximity (just mere centimeters away) to an accelerometer-equipped cell phone. The keystrokes were detected using only the vibration and not the sound of the key being pressed.
Other methods of seismic hacking include the use of a computer system’s speakers to create low-frequency sounds, which in turn produce intelligible vibrations that can be picked up by a nearby accelerometer.
Magnetic
Virtually all current smart devices have some form of a magnetometer chip which serves as a compass and has the ability to measure the magnetic fields, thus detecting true north and south. However, a sensor like this can also be abused and transformed into a communication channel.
The hypothesis of a malware receiving commands via a magnetometer has been previously explored and it has been proven that error-free communication, using a custom-built electro-magnet which induces changes in the magnetic field of the targeted device, can happen relatively easily up to 3.5 inches, but greater distances are also possible with a stronger electromagnet.
Electromagnetic
Electromagnetic radiation emissions are practically omnipresent in all electronic equipment, especially if is unshielded.
The Van Eck phreaking methodology, named after Dutch computer researcher Wim van Eck, allows an eavesdropper to clone a CRT monitor’s contents by remotely detecting its electromagnetic (EM) emissions. In an unshielded CRT monitor, tests were successfully conducted from a distance of 1km as well as a distance of 200m for a shielded monitor.
Additionally, all video cards leak tremendous amounts of EM emissions, which can be manipulated to transmit data. “AirHopper” is an example of a malware that turns a computer’s video card into an FM transmitter, which can be captured by a standard FM radio, even the ones that are built into a smartphone.